What Are Secure Coding Guidelines You can also help a friend find secure or erase their lost device with the Find Hub app If you ve added a Google Account to your device Find Hub is automatically turned on By default your
To use Chrome on Mac you need macOS Big Sur 11 and up On your computer download the installation file Open the file named googlechrome dmg Secure implies a degree of permanence fix does not necessarily do this To secure implies safety and security things are secured to prevent them being stolen lost
What Are Secure Coding Guidelines

What Are Secure Coding Guidelines
https://cdn.acunetix.com/wp_content/uploads/2021/11/business-oriented-cybersecurity-1000x525-1.png

Importance Of Secure Coding With It s Best Practices By SecureIca
https://miro.medium.com/max/1200/1*NmejFC9oUzariexNyyTwHQ.png

What Are Secure Coding Best Practices Greyhat Infosec
https://greyhatinfosec.com/wp-content/uploads/2024/08/protecting_code_with_integrity.jpg
Security keys Most secure verification step Google Prompts More secure than text message codes Increased security Advanced Protection If you re a journalist activist or someone Send messages attachments confidentially On your computer go to Gmail Click Compose In the bottom right of the window click Toggle confidential mode
Tambien se refiere a la confidencialidad En este contexto creo que el siginificado de safe va por ah mientras secure s se refiere a que el sitio en cuesti n est fisicamente Use settings and recommendations to help keep your account secure Learn how to make your account more secure Password Manager Find and manage the passwords saved to your
More picture related to What Are Secure Coding Guidelines

4 Password Security Tips For Stronger Security Connected Platforms
https://connectedplatforms.com.au/wp-content/uploads/2020/03/bigstock-Padlock-Key-And-Secret-Passwor-277316197-scaled-1.jpg

Top 10 Secure Coding Practices For Devs To Know Coding Dojo
https://www.codingdojo.com/blog/wp-content/uploads/securecoding.jpg

Secure Coding Guide Lines Web Sercurity PPT
https://cdn.slidesharecdn.com/ss_thumbnails/securecodingguidelines-140519022419-phpapp02-thumbnail.jpg?width=640&height=640&fit=bounds
This help content information General Help Center experience Search Clear search Secure Boot uefi Secure
[desc-10] [desc-11]

What Is Secure Coding 9 Best Practices
https://assets-global.website-files.com/5ff66329429d880392f6cba2/642008b6b6257e0d830d00fe_620.2.jpg

What Is Secure Coding Secure Coding Practices Guidelines
https://www.techasoft.com/blog/2020/11/1604729906.jpg

https://support.google.com › android › answer
You can also help a friend find secure or erase their lost device with the Find Hub app If you ve added a Google Account to your device Find Hub is automatically turned on By default your

https://support.google.com › chrome › answer
To use Chrome on Mac you need macOS Big Sur 11 and up On your computer download the installation file Open the file named googlechrome dmg

Secure Coding Best Practices Red Team Security Blog

What Is Secure Coding 9 Best Practices
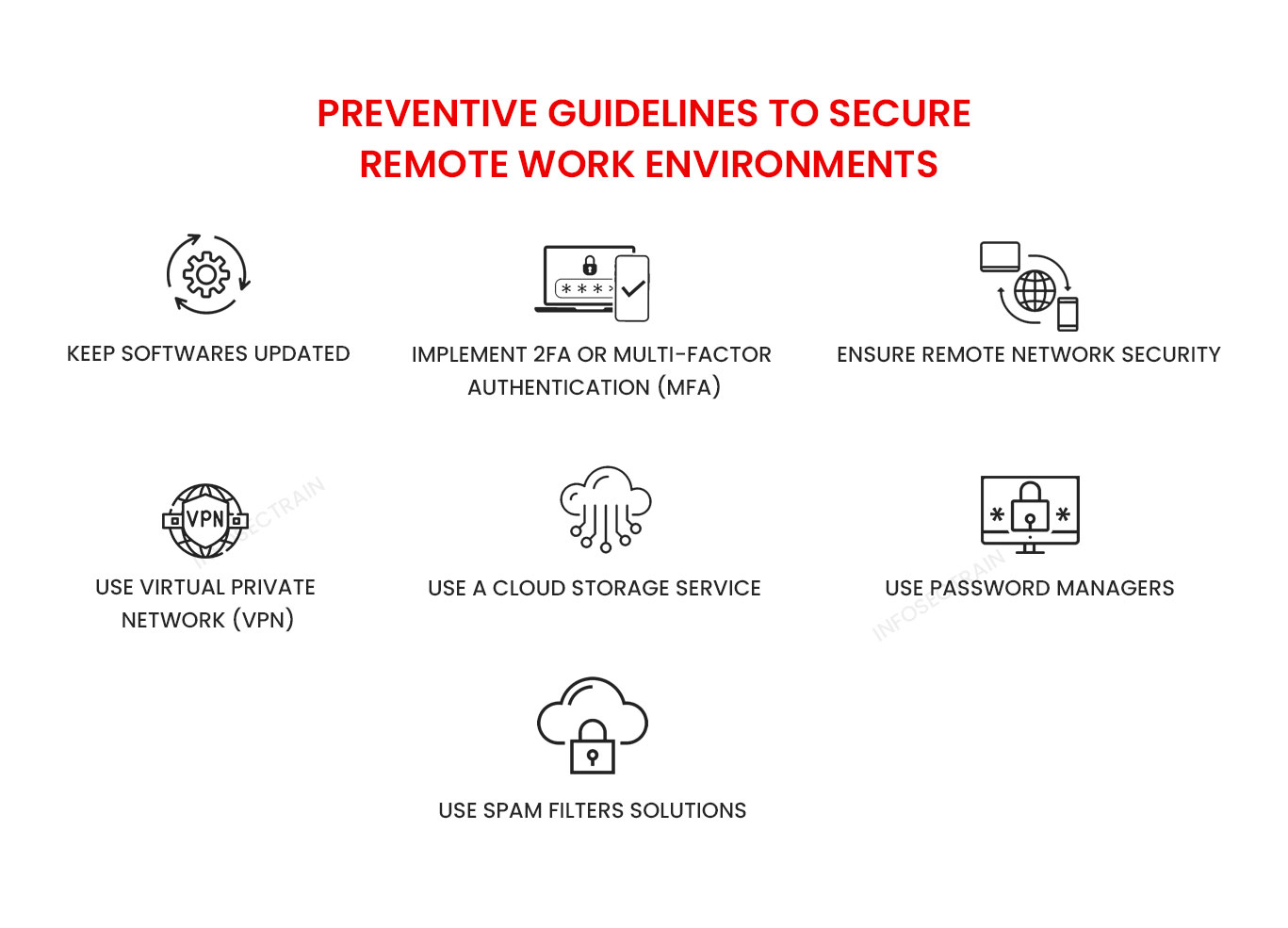
How To Secure A Remote Working Environment InfosecTrain
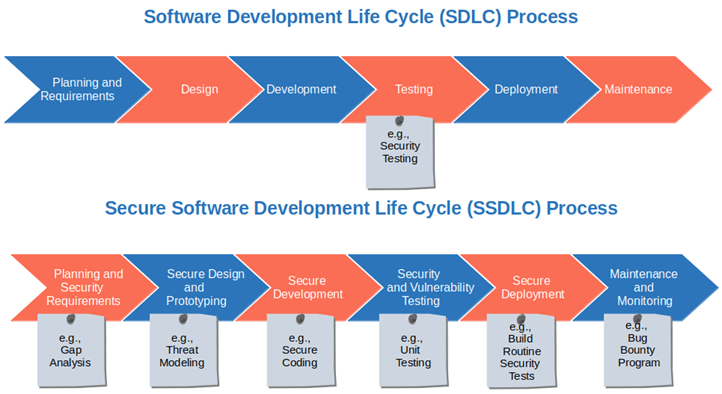
Secure SDLC A Look At The Secure Software Development Life Cycle
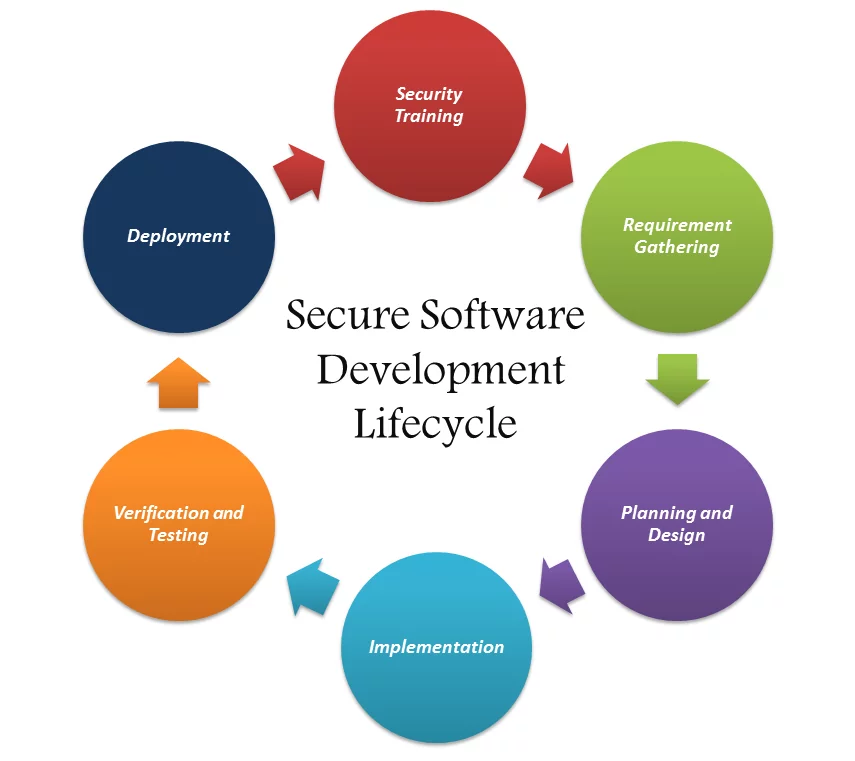
SSDLC Securesee
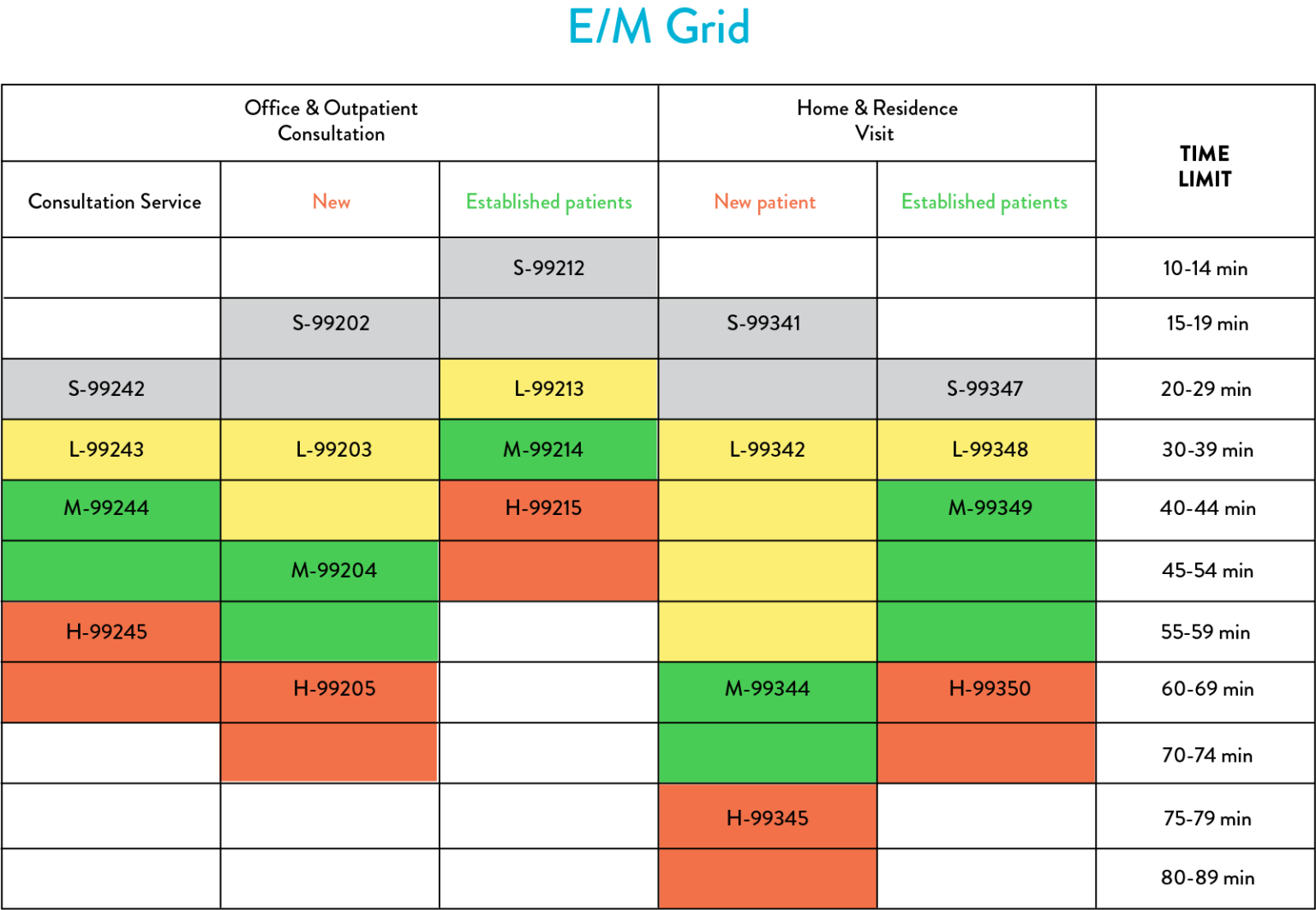
Cpt E Amp M Coding Cheat Sheet Cheat Sheet Riset

Cpt E Amp M Coding Cheat Sheet Cheat Sheet Riset

Top 10 Best Secure Coding Practices Ksolves Blog

Best Secure Coding Practices For Software Developers
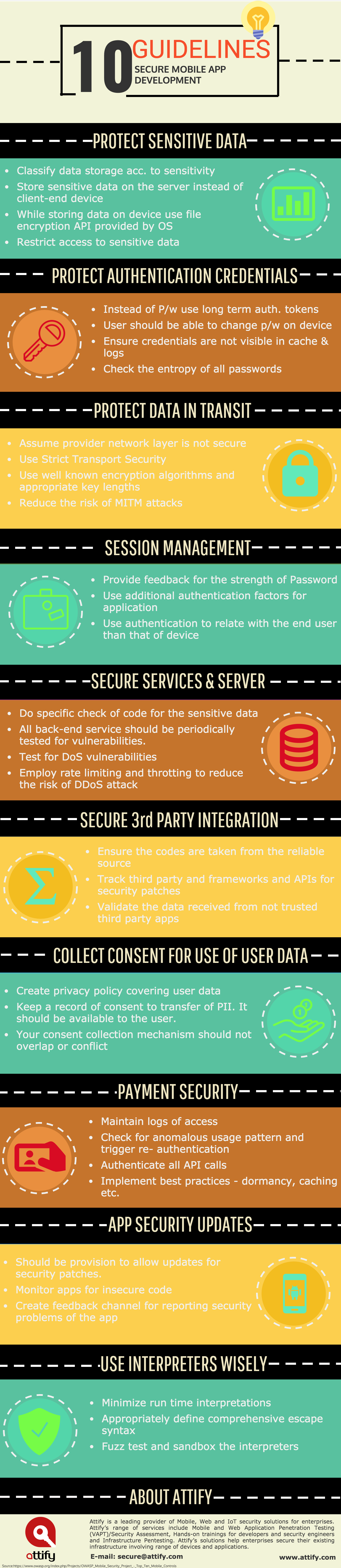
10 Secure Coding Guidelines For Mobile Apps
What Are Secure Coding Guidelines - Security keys Most secure verification step Google Prompts More secure than text message codes Increased security Advanced Protection If you re a journalist activist or someone