What Are Secure Coding Practices Send messages attachments confidentially On your computer go to Gmail Click Compose In the bottom right of the window click Toggle confidential mode
If you notice unfamiliar activity on your Google Account Gmail or other Google products someone else might be using it without your permission If you think your Google Account or Gmail have been hacked follow the steps below to help spot suspicious activity get back into your account and make it more secure This help content information General Help Center experience Search Clear search
What Are Secure Coding Practices

What Are Secure Coding Practices
https://cdn.acunetix.com/wp_content/uploads/2021/11/business-oriented-cybersecurity-1000x525-1.png

What Is Secure Coding Secure Coding Practices Guidelines
https://www.techasoft.com/blog/2020/11/1604729906.jpg

Top 10 Secure Coding Practices For Devs To Know Coding Dojo
https://www.codingdojo.com/blog/wp-content/uploads/securecoding.jpg
You can also help a friend find secure or erase their lost device with the Find Hub app If you ve added a Google Account to your device Find Hub is automatically turned on By default your device is set to the With network in high traffic areas only setting so that it stores encrypted recent locations with Google and helps find offline devices as part of a crowdsourced network Visit the Google Play Developer Policy Center for guidance on protecting user privacy and providing a safe and secure environment for users Learn more about Google policy on Unwanted Software If you believe that your app was incorrectly flagged or
If you forgot your password or username or you can t get verification codes follow these steps to recover your Google Account Default Secure Info or Not secure Not secure or Dangerous To find a summary of the site s privacy details cookies and site data permissions history of visits and information about the page select the icon To find out more about the source and other perspectives on the page s topics select About this page Learn more about About this
More picture related to What Are Secure Coding Practices

10 Secure Coding Practices Standards Policy Techniques
https://www.infinijith.com:3443/storage/blog/90/large.png

A Guide To OWASP s Secure Coding Practices Checklist
https://codesigningstore.com/wp-content/uploads/2023/06/owasp-secure-coding-practices-checklist-feature-jpg.webp
Secure Coding Practices Every Developer Should Know HackerNoon
https://hackernoon.imgix.net/images/OHYkX14AfEgwn2U06uGItMBzFDm1-6993rhk.jpeg
This help content information General Help Center experience Search Clear search This help content information General Help Center experience Search Clear search
[desc-10] [desc-11]

Top 10 Best Secure Coding Practices Ksolves Blog
https://www.ksolves.com/wp-content/uploads/1280-x-711_Secure-Coding__500x750-scaled.jpg

Fostering Secure Coding Practices For Web Applications Invicti
https://cdn.invicti.com/app/uploads/2022/06/28120538/secure-coding-practices-1024x538.png

https://support.google.com › mail › answer
Send messages attachments confidentially On your computer go to Gmail Click Compose In the bottom right of the window click Toggle confidential mode

https://support.google.com › accounts › answer
If you notice unfamiliar activity on your Google Account Gmail or other Google products someone else might be using it without your permission If you think your Google Account or Gmail have been hacked follow the steps below to help spot suspicious activity get back into your account and make it more secure

Secure Coding Practices For 2023 Writing Code With Security In Mind

Top 10 Best Secure Coding Practices Ksolves Blog

Landing Template 2023 Cydrill Software Security

Secure Coding Practices Writing Secure Software YouTube

Secure Coding Best Practices SecureCoding

What Is Secure Coding And Why Is It Important VPNOverview 2022

What Is Secure Coding And Why Is It Important VPNOverview 2022

Best Secure Coding Practices For Software Developers
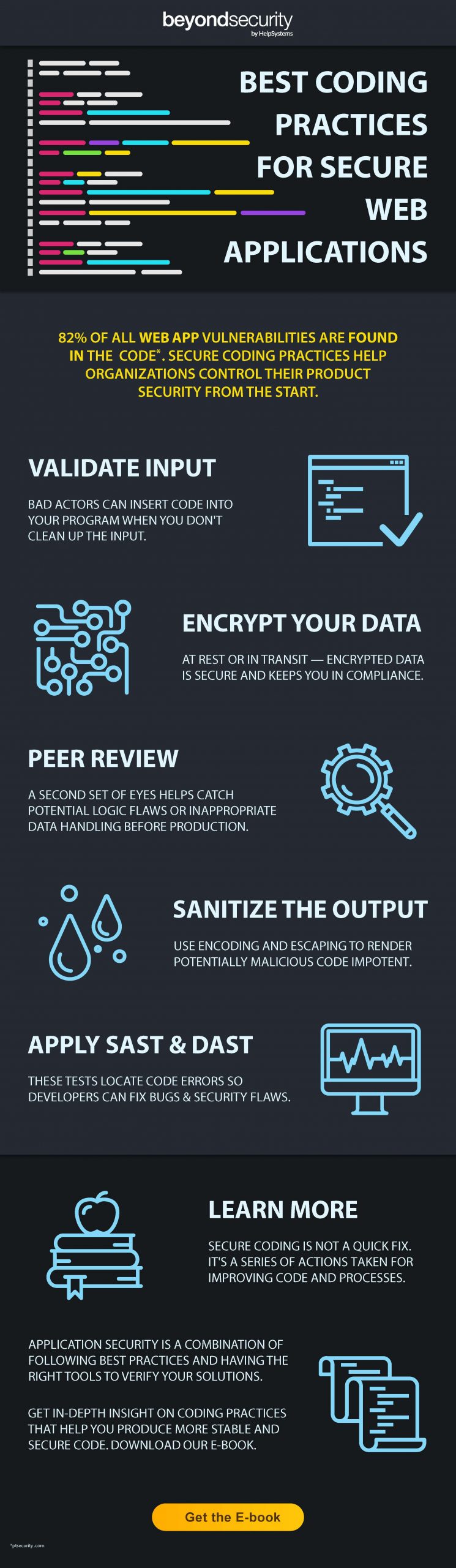
Best Secure Coding Practices For Web Applications Beyond Security

Importance Of Secure Coding With It s Best Practices By SecureIca
What Are Secure Coding Practices - Default Secure Info or Not secure Not secure or Dangerous To find a summary of the site s privacy details cookies and site data permissions history of visits and information about the page select the icon To find out more about the source and other perspectives on the page s topics select About this page Learn more about About this