Expand 5 3y 2 5 2y 3 Today March 23rd 2017 WikiLeaks releases Vault 7 Dark Matter which contains documentation for several CIA projects that infect Apple Mac firmware meaning the infection
Today August 24th 2017 WikiLeaks publishes secret documents from the cyber operations the CIA conducts against liaison services which includes NSA DHS and FBI 2017 02 04 WikiLeak s publication of Vault 7 begins its new series of leaks on the U S Central Intelligence Agency Code named Vault 7 by WikiLeaks it is the largest ever publication of
Expand 5 3y 2 5 2y 3
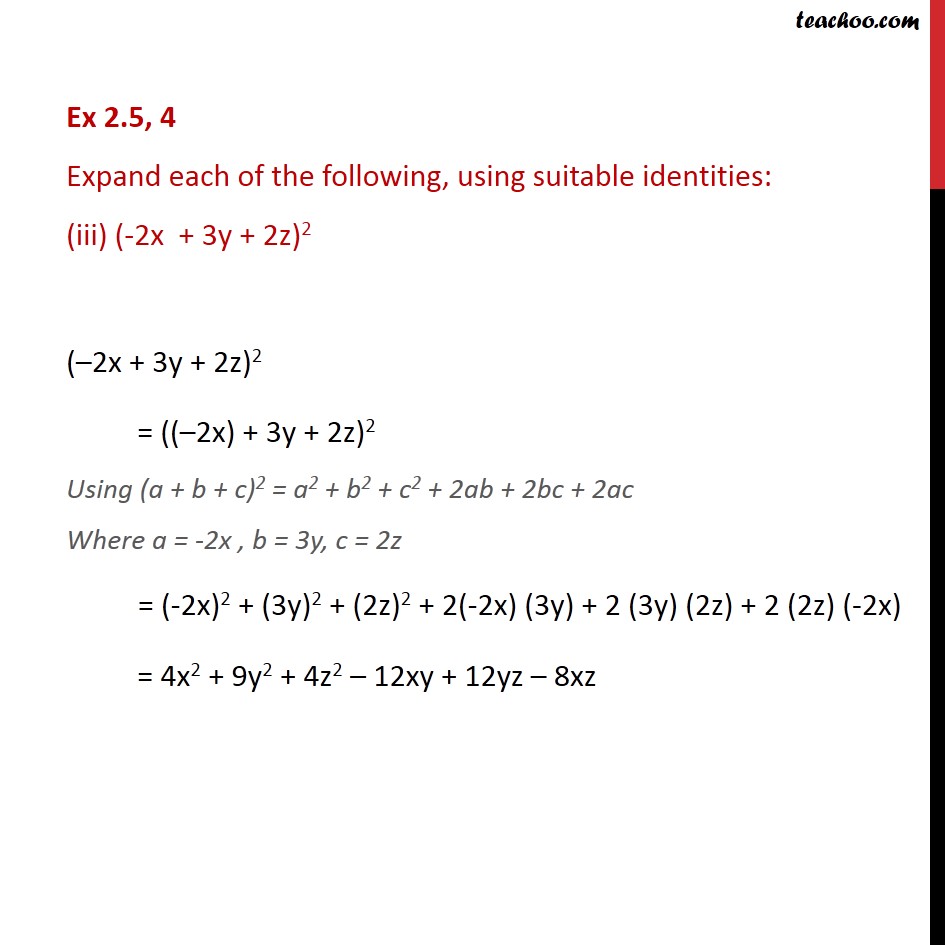
Expand 5 3y 2 5 2y 3
https://d77da31580fbc8944c00-52b01ccbcfe56047120eec75d9cb2cbd.ssl.cf6.rackcdn.com/9e0a2c68-d286-4aa0-a169-19a6b61be6eeslide14.jpg
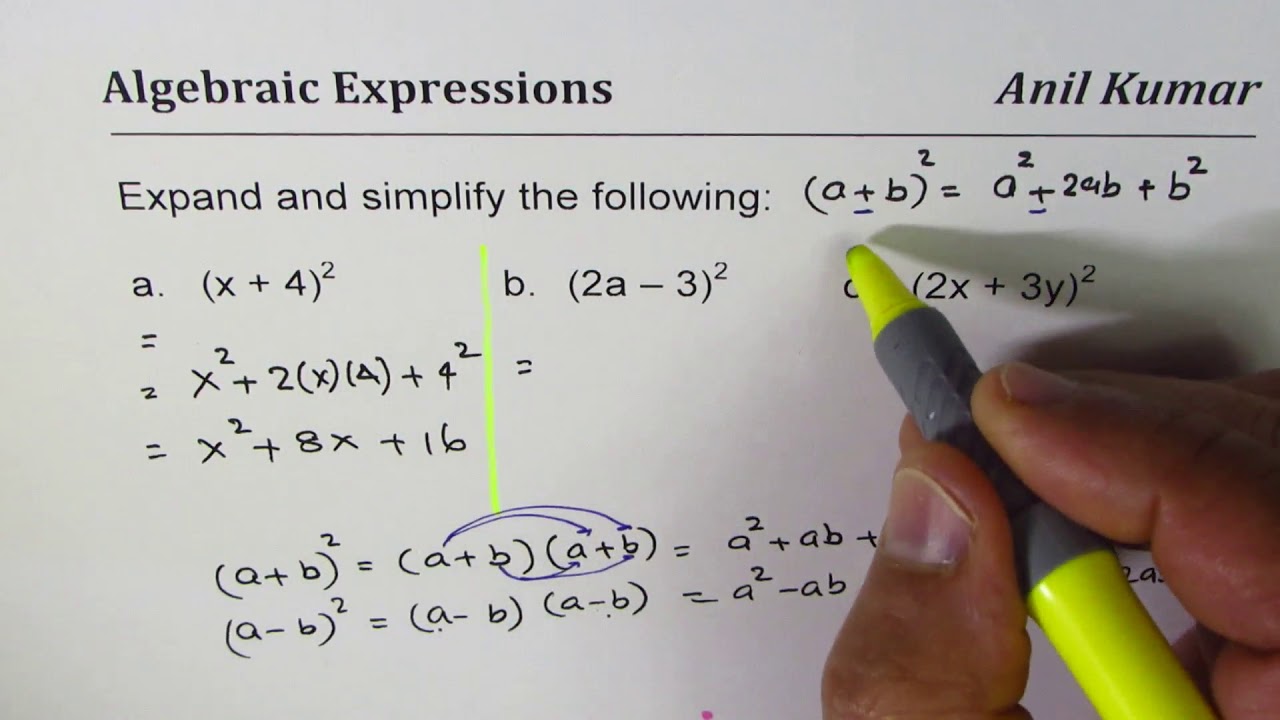
Expand And Simplify Binomial Squares 2x 3y 2 YouTube
https://i.ytimg.com/vi/YASxKwOa-ow/maxresdefault.jpg
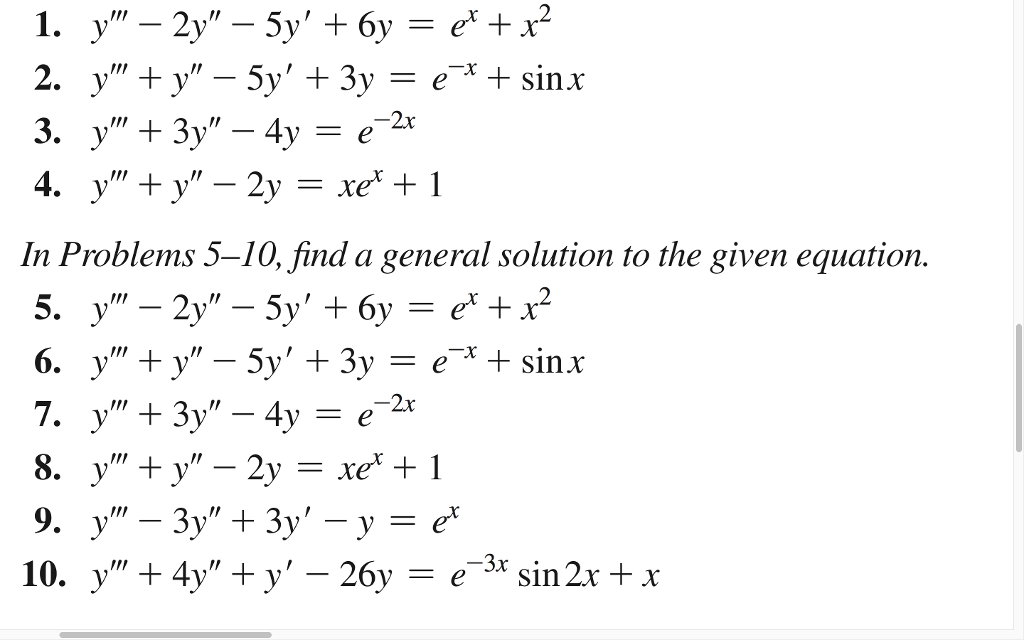
Solved Transcribed Image Text 1 Y 2y 5y 6y E X2 2
https://files.transtutors.com/book/qimg/34f75936-4c4b-4c40-a65f-e80eeabc6f50.png
Today 5th August 2021 WikiLeaks publishes The Intolerance Network over 17 000 documents from internationally active right wing campaigning organisations HazteOir and CitizenGO Today August 3rd 2017 WikiLeaks publishes documents from the Dumbo project of the CIA enabling a way to suspend processes utilizing webcams and corrupt any video recordings
Vault 8 Source code and analysis for CIA software projects including those described in the Vault7 series This publication will enable investigative journalists forensic How to contact WikiLeaks What is Tor Tips for Sources After Submitting Vault 7 CIA Hacking Tools Revealed Releases Documents Navigation
More picture related to Expand 5 3y 2 5 2y 3

The Equation Of Line Passing Through The Point Of Intersection Of The
https://toppr-doubts-media.s3.amazonaws.com/images/3851565/3de1821a-109d-44f6-be1d-5f3cd39a10d5.jpg

Given That 3 4 2x 5 3y x And 3 x y 25 2y 1 1 How To Show X
https://useruploads.socratic.org/xRHAJiCrTDiBc9u2ScUI_log.jpeg
If 3x 5y 9 And 5x 3y 7 Then What Is The Value Of X Y
https://d1hj4to4g9ba46.cloudfront.net/questions/1176995_1343668_ans_bc0e523fa69a4c55b5453f6be62e9e35.JPG
CIA espionage orders for the 2012 french presidential election Feb 16 2017 All major French political parties were targeted for infiltration by the CIA s human HUMINT and electronic Today August 3rd 2017 WikiLeaks publishes documents from the Dumbo project of the CIA enabling a way to suspend processes utilizing webcams and corrupt any video recordings
[desc-10] [desc-11]

Expand Using Identity 2x 3y 3
https://d1hj4to4g9ba46.cloudfront.net/questions/1294382_1609038_ans_cac3be2bf58d4eb1ae0160f7a59e820b.jpg

Expand Each Of The Following Using Suitable Identities x 2y 4z 2 2x
https://i.ytimg.com/vi/sagTJYEx6cE/maxresdefault.jpg

https://wikileaks.org
Today March 23rd 2017 WikiLeaks releases Vault 7 Dark Matter which contains documentation for several CIA projects that infect Apple Mac firmware meaning the infection

https://wikileaks.org › +-Intelligence-+.html
Today August 24th 2017 WikiLeaks publishes secret documents from the cyber operations the CIA conducts against liaison services which includes NSA DHS and FBI
Solved 4 Dx dt 2x 3y 8 Dy dt 3x 2y 12 5

Expand Using Identity 2x 3y 3

3x 2y 4 2x 3y 7 By Elemenation Method Brainly in

2x 3y 2x 3y Solve Using Identities Brainly in

2y 3y 2y 0 Y 0 1 Y 0 3 YouTube

Example 17 Solve By Matrix Method 3x 2y 3z 8 2x y z 1 Examples

Example 17 Solve By Matrix Method 3x 2y 3z 8 2x y z 1 Examples

Solve By Cross Multiplication 2x Y 5 And 3x 2y 8 Video

Solve 2y 5y 3y 0 YouTube
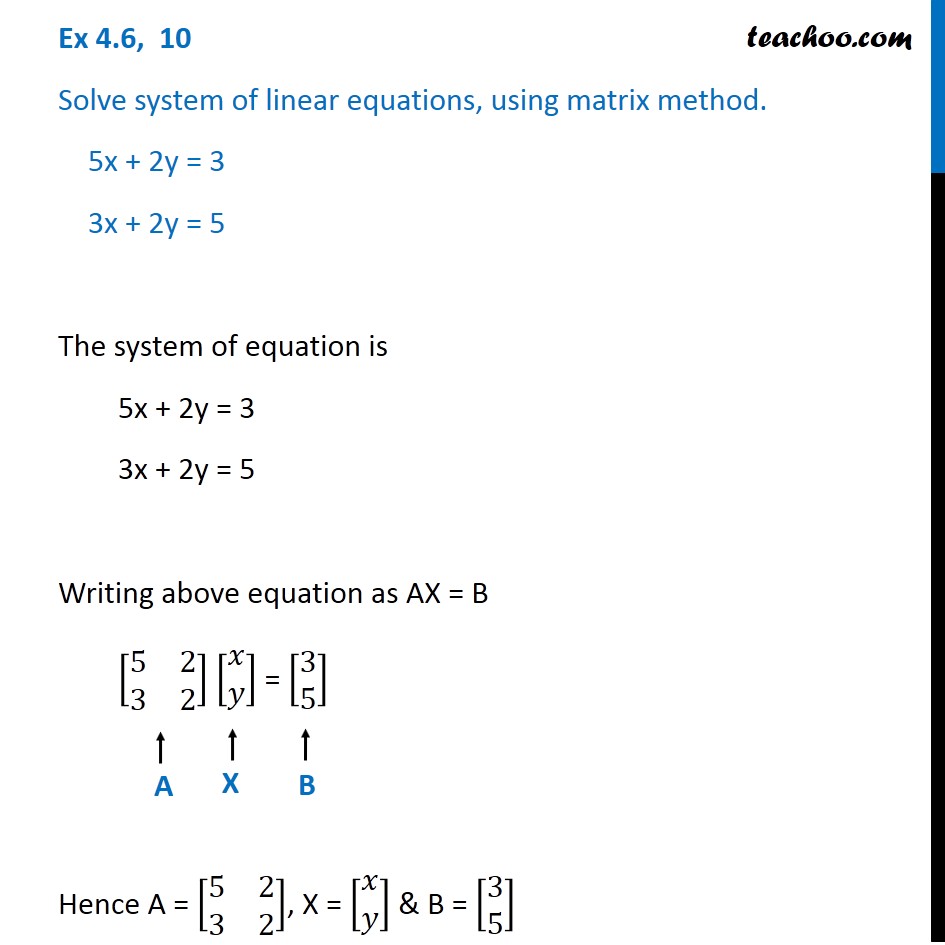
Ex 4 6 10 Solve Using Matrix Method 5x 2y 3 3x 2y 5 Find Solution
Expand 5 3y 2 5 2y 3 - How to contact WikiLeaks What is Tor Tips for Sources After Submitting Vault 7 CIA Hacking Tools Revealed Releases Documents Navigation
